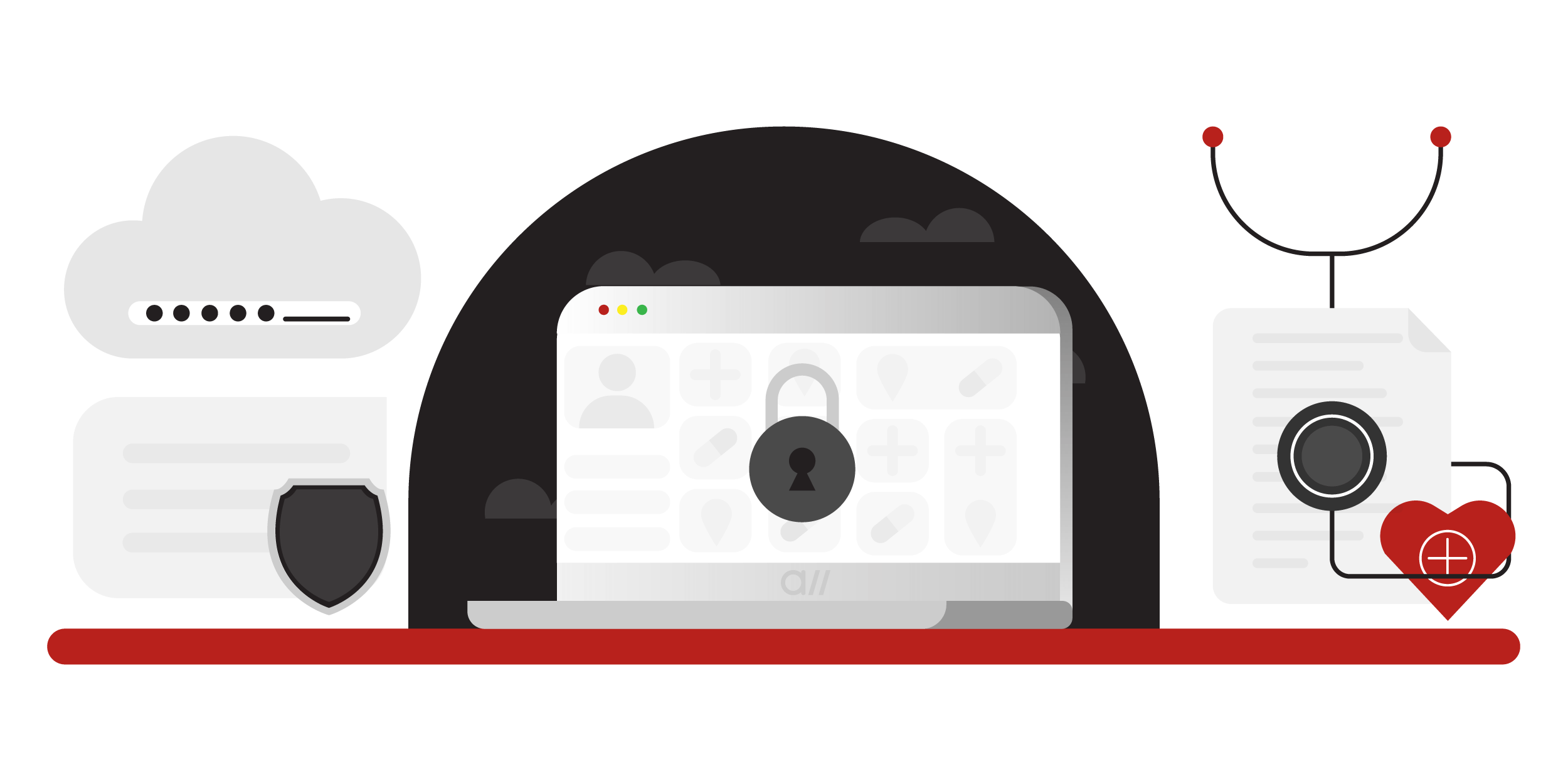
Top 5 Data Security Threats to Healthcare
Every aspect of daily life has been permeated by technological progress: the “traditional” way of doing things, from even a generation ago, is now rendered obsolete and antiquated by the digital revolution.
Accordingly, the healthcare industry is optimizing online options by shifting data from physical, analog systems to cloud-based formats. Instantaneous internet access can help you locate just about anything related to healthcare, whether it’s about reading ESA doctors review or looking up the appropriate doctor or facility for your medical needs, you can find this information in just the click of a button.
Nevertheless, the appeal of adopting the latest technology to healthcare systems must be tempered by paying special attention to the following data security threats.
1. Extensive Access by Staff
At medical institutes, multiple healthcare personnel have unimpeded access to the patient’s digital profile, putting sensitive personal information at risk. Although the vast majority of hospital employees would never consider such behavior, just one violation can provoke costly litigation and erosion of public trust in your institution.
Health information that is left vulnerable is an easy target to thieves eager to take advantage of your stolen data. Thriving criminal markets exist for sensitive health-related and financial information that can be used for blackmail and fraud.
2. Poor Data Security & Cybercrime
Despite the level of protection extended to your software and practices, cyber-criminals may try to compromise your data. Such violations, both global and local, appear in news headlines on a daily basis and result in severe punishment.
Inevitably, an attempt will be made to protect the healthcare data held by your organization. This requires a multi-tiered approach to securing patient information from unauthorized viewing and sharing.
Hackers use basic approaches which help them manipulate employees and acquire patient information. One example is by sending an email from a seemingly legitimate company, created to lure people into providing customer login credentials.
3. Access Through Mobile Devices
Now that mobile devices are the preferred means for accomplishing daily tasks, healthcare providers must strive to enable user-friendly sites for patients and partners, while maintaining the utmost security. Some healthcare facilities also extend their in-house services to remote interfaces via phone, tablet, or laptop for increased mobility and efficiency.
The free flow of information offered by mobile devices is not without detriment. In addition to the threat from within that exposes personal data to malware; loss, damage, theft, or improper disposal of our phones open us up to further risk and security threats.
4. Lack of Knowledge
Facilities without robust, up to date security practices have a higher risk of data breaches. Although IT teams create the protocols and systems, it is not solely responsible for preventing infringement; the collective education and effort of every team member must be taken into account to ensure that best practices are internalized.
For example, healthcare staff cannot stay logged in to accounts, always signing out of the system when leaving a workspace. Similar, simple precautions fortify data security, which is why all authorized staff need training on data security procedures before obtaining login credentials.
5. Unrestricted Access to Data Devices
One of the major causes of data theft is unauthorized use of tablets, laptops, and desktop computers owned by the healthcare facility. . .
Restricted access to digital devices is essential to augment data security within the physical building. Healthcare providers can invest in this aspect of their security system by adding biometric verification systems and security cameras.
How to address data security threats in your healthcare business?
If any of the 5 security threats above raise any concerns, take action immediately by contacting your IT team or healthcare development partner. The Health Insurance Portability and Accountability Act (HIPAA) requires that all healthcare facilities conduct a risk assessment to ensure entire compliance and that all systems within the establishment are invulnerable.
The risk analysis will indicate where your company’s software is exposed to security threats. With the proper guidance, implementation, and maintenance, you can count on the maximum protection for healthcare data and circumvent adversity.

A self-motivated digital marketing specialist with 3+ years of experience advertising in the financial services industry.
While I wear several marketing hats, my primary focus is on content strategy and curation.
I aim to consistently challenge myself and position my skills toward personal and professional endeavors that lead to measurable results.